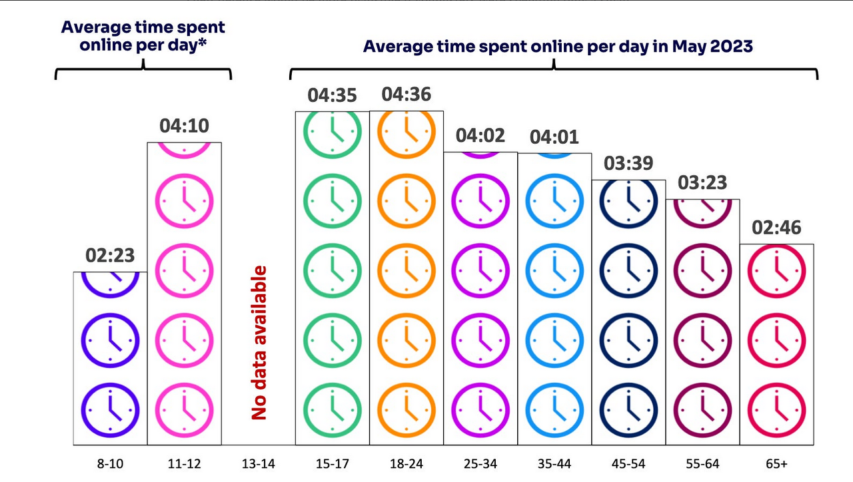
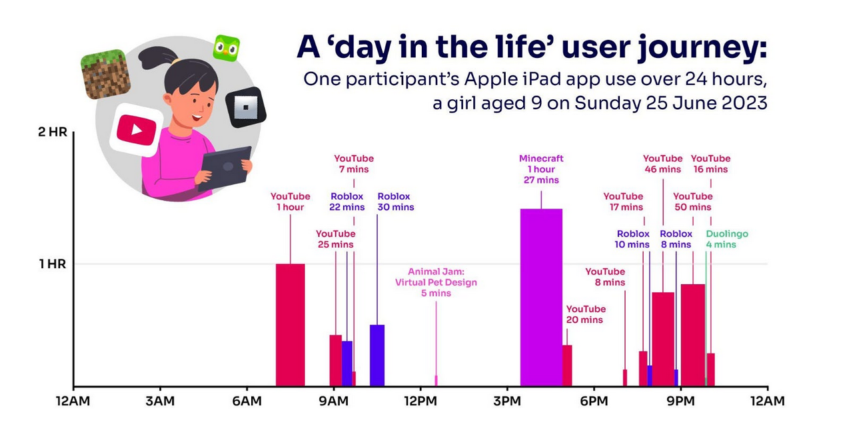
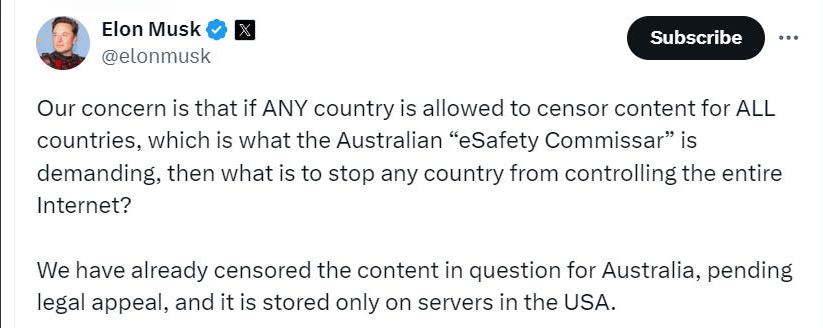
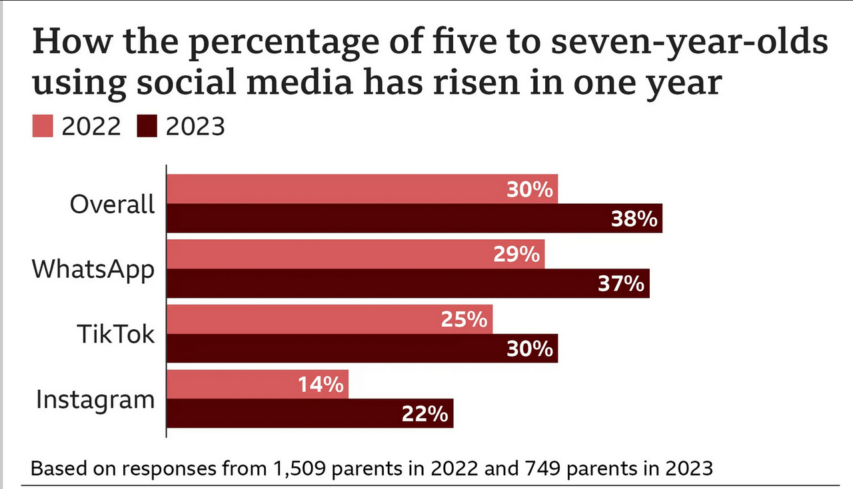Freddie deBoer considers systems that have been overoptimized to the detriment of most users and the benefit of a small, privileged minority:
I know a guy who used to make his living as an eBay reseller. That is, he’d find something on eBay that he thought was underpriced so long as the auction didn’t go above X dollars, buy it, then resell it for more than he paid for it Classic imports-exports, really, a digital junk shop. Eventually he got to the point where, with some items, he didn’t ever have physical possession of them; he had figured out a way to get them directly from whoever he bought an item from to the person he had sold the item to, while still collecting his bit of arbitrage along the way. This buying and selling of items on eBay, looking for deals, was sufficient to be his full-time job and pay for a mortgage. But the last time I saw him, a few years ago, he had gotten an ordinary office job. He told me that it had become too difficult to find value; potential sellers and buyers alike had access to too many tools that could reveal the “real” price of an item, and there was little delta to eke out. He’s not alone. If you search around in eBay-related forums, you’ll find that many longtime sellers have reached similar conclusions. The hustle just doesn’t work anymore.
I don’t suppose there’s any great crime there — it’s all within the rules. And there does appear to still be an eBay-adjacent reselling economy; it’s just that, as far as I can glean, it’s driven by algorithms and bots that average resellers simply don’t have access to. It appears that some super-resellers have implemented software solutions to identify underpriced goods and buy them automatically and algorithmically. They have optimized the system for their own use, giving them an advantage, putting other sellers at a disadvantage, and arguably hurting buyers by eliminating uncertainty that sometimes results in lower-than-optimal-to-sellers prices. This is all in sharp contrast to the early years, when my friend would keep listings for lucrative product categories open – in separate windows, not tabs, that’s how long ago this was – and refresh until he found potential moneymakers. That sort of human searching and bidding work stands at a sharp disadvantage compared to those with information-scraping capacity and automated tools. It’s a good example of how access to data has left systems overoptimized for some users. One of the things that the internet is really good at is price discovery, and these digital tools help determine the “optimal” price of items on eBay, which results in less opportunity for arbitrage for other players.
My current working definition of overoptimization goes like this: overoptimization has occurred when the introduction of immense amounts of information into a human system produces conditions that allow for some players within that system to maximize their comparative advantage, without overtly breaking the rules, in a way that (intentional or not) creates meaningful negative social consequences. I want to argue that many human systems in the 2020s have become overoptimized in this way, and that the social ramifications are often bad.
Getting a restaurant reservation is a good example. Once upon a time, you called a restaurant’s phone number and asked about a specific time and they looked in the book and told you if you could have that slot or not. There was plenty of insiderism and petty corruption involved, but because the system provided incomplete information that was time consuming to procure, there was a limit to how much you could game that system. Now that reservations are made online, you can look and see not only if a specific slot has availability but if any slots have availability. You can also make highly-educated guesses about what different slots are worth on the market through both common sense (weekend evenings are the most valuable etc) and through seeing which reservations get snapped up the fastest in an average week. And being online means that the reservation system is immediate and automatic, so you can train a bot to grab as many reservations as you want, near-instantaneously, and you can do so in a way that the system doesn’t notice. (Unlike, say, if you called the same restaurant over and over again and tried to hide your voice by doing a series of fake accents.) The outcome of all this is that getting a reservation at desirable places is a nightmare and results in a secondary market that, like seemingly everything in American life, is reserved for the rich. The internet has overoptimized getting a restaurant reservation and the result is to make it more aggravating and less egalitarian.
As has been much discussed, nearly the exact same scenario has made getting concert tickets a tedious and ludicrously-pricy exercise in frustration.