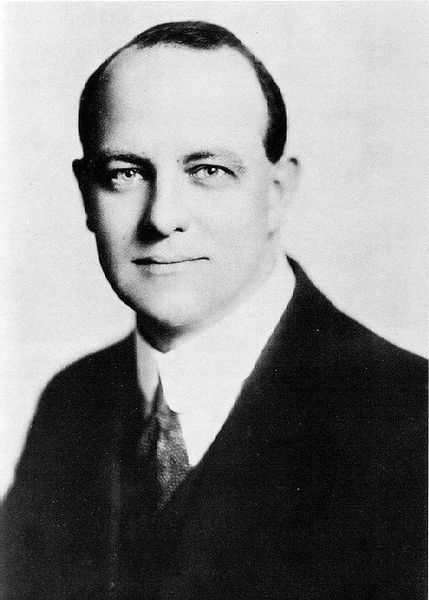One of the things people have always believed about modern media is that video beats audio and audio beats the written word. Before the rise of “new media” on the internet, this meant television was better than radio and radio better than newspapers. In the internet age, the assumption now is that live streamers have greater reach than podcasters and podcasters have a greater reach than bloggers. Mixed in there are people who exist only as entities on social media platforms.
One reason for this assumption is youth culture. In liberal democracy, the young are treated like gods, in the same way novel social ideas are treated as gifts from the gods, so whatever young people like is heralded as pure and beautiful. Young people, especially children, are first drawn to images, then sounds and finally as they mature into adults, the written word. In modern liberal democracies, therefore, video platforms are treated like sacred altars where our most sacred members perform.
The youth culture phenomenon has co-evolved with the rise of mass media. In the days before mass media, young people were at the bottom of the cultural hierarchy. The first flicker of youth culture in America was the jazz age, but even there the people driving it were old by modern standards. The characters in The Great Gatsby, for example, are mostly early middle-aged. It was after the war with the explosion of Hollywood that youth culture blossomed into the centerpiece of modern life.
Another reason why video maintains a privileged place at the top of our social hierarchy is Baby Boomer culture. For Boomers, for whom mass media evolved, video was always the top. In the golden age of television, for example, the whole country would watch popular television programs. No newspaper or radio broadcaster had the reach of a popular television program. Hitting the big time in the field of news or entertainment meant getting on TV or in the movies.
As much as young people, and not so young people, complain about the Baby Boom generation, the Boomers still control the culture. That is plainly obvious with the panic over the Chinese virus. If the Boomers were twenty years younger, the virus would rate a few mentions in the New York Times science section. Since Boomers are now deeply involved in the health care system, anything medical is going to be of utmost importance to everyone. It is why nurses are now heroes.
The Z Man, “Thoughts on Modern Media”, The Z Blog, 2020-05-09.
May 13, 2025
QotD: The song is correct – video did kill the radio star
December 7, 2024
Aftermath: December 8
The History Guy: History Deserves to Be Remembered
Published 8 Dec 2021December 7, 1941 is remembered as the date that will live in infamy, but that term was spoken by President Franklin Roosevelt on December 8th. Nowhere was the weight of history more obvious than in the territory of Hawaii.
(more…)
November 3, 2024
QotD: Minutemen
Ten years ago, America’s right-wing paramilitaries were so anti-government, they thought that driver’s licenses were an unbearable infringement on their liberties. Now they’re out on the border HELPING THE FEDS ENFORCE THEIR REGULATIONS. What the hell’s up with that?
Granted, there’s not necessarily much overlap between the two groups. But one has supplanted the other in the mass media, the public imagination, and the affection of the right-wing radio hosts — and so help me, I think I miss the days when I felt a certain kinship with the crazies.
Jesse Walker, “More ’90s Nostalgia”, Hit and Run, 2005-07-28.
September 21, 2024
“This might be the greatest asymmetrical attack in human history”
Terrorist organizations in the Middle East always have to be aware of the risk of coming to the attention of Israel accidentally, and they’ve suffered losses whenever their operations have been prematurely exposed. The attack on Hezbollah’s communications infrastructure is, as Phil A. McBride says in The Line, “something genuinely new in warfare”:

The attack on Hezbollah’s communications through exploding pagers, radios, and other electronic devices triggered a cascade of instant memes.
Detonating the pagers and other devices would have been a relatively easy thing to do (to the extent that any of this was easy!), since it’s obvious that Israel had already penetrated the pager network, and Hezbollah’s communications generally, before the devices were even deployed. Once Israel was confident that they’d put all the devices into the right hands, they simply sent a message — remember, these devices are all intended to receive telecommunications — that somehow triggered the explosions we saw. I don’t know if the explosives did all the damage, or if the batteries were somehow overloaded as well. What is clear is that the explosions were enough to kill, injure and maim people who were directly holding the devices, but not much more. Videos posted online show people suddenly dropping to the ground in agony after their device explodes in their hands, pockets or backpacks, but people in their immediate vicinity are unharmed.
Again, none of this is easy, but if one is looking to remotely detonate a bomb, it helps when the bomb it intended to literally receive incoming communications.
[…]
That covers the pagers and two-way radios, but what about the other various items that exploded? While almost everything electronic you can buy these days has internet/wireless capability, Hezbollah went through a lot of trouble to be as disconnected from the internet as possible. I can only assume they wouldn’t have connected a device meant to read the fingerprints of terrorists trying to enter a safe house to the internet, where a Mossad hack is a constant threat. This means that any other device that exploded not only had explosive charges installed, but also a radio capable of receiving a remote detonation command. The most efficient approach would have been to tune those radios to the same frequencies used by Hezbollah’s two-way radios to minimize the infrastructure needed to pull off what was already an insanely complex operation, but we will need more information to even begin to understand that part of Israel’s plan.
And let’s talk about the plan. The level of sophistication for such an operation cannot be understated. Everything that we’ve seen over the last few days indicates a complete and total breakdown of Hezbollah’s internal security. Israel managed to intercept and infiltrate both their primary and backup communications networks before they were even deployed, as well as a swath of other electronic equipment, and turn them into bombs.
It has been said that communication is the most important component of any military system, but I don’t think anyone had ever thought of actually weaponizing the opposition’s communications infrastructure itself before now. This is something genuinely new in warfare.
August 18, 2024
Hirohito Announces Surrender – War Continues – WW2 – Week 312 – August 17, 1945
World War Two
Published 17 Aug 2024Hirohito broadcasts Japan’s surrender to the world- despite an attempted to coup to prevent it from happening, and much of the world celebrates, but the war isn’t really over. The Soviets are busy invading Manchuria, and there’s revolution in Vietnam and Indonesia.
00:00 Intro
00:22 Recap
00:49 Attempted Coup In Japan
04:12 Hirohito Surrenders
08:54 Japanese Surrender In China
12:05 Soviets In Manchuria
17:52 Revolution In Vietnam
20:33 Summary
21:07 Conclusion
(more…)
July 13, 2024
The BBC – the Biased Broadcasting Corporation
Like Canada’s CBC, the BBC considers itself to be more than just a TV, Radio, and online broadcaster. From its founding in the early 1920s, the BBC has taken upon itself the role of teacher, moral example, and moulder of public opinion. The BBC has always been more progressive in most senses than the British public (as the CBC has been in Canada), but over the last few decades, the BBC has been hurtling leftward on gender issues faster than ever before:
Complaints about BBC impartiality are nothing new. The state broadcaster has a kind of constitution in the form of its Royal Charter, by which it is required to maintain due impartiality in its news reporting and when it comes to controversial subjects. But does it succeed?
In holding politicians from the left and the right to account in its reporting, accusations of bias are always likely to occur. Some people claim the BBC is inherently left-leaning, others claim it is inherently right-leaning. It really depends on your perspective. For my part, I believe that BBC does a generally good job — with a few notable lapses — when it comes to political impartiality.
However, where I think it clearly fails is in regard to its ideological impartiality. When it comes to the ideology of Critical Social Justice, what has become known colloquially as the “woke” movement, the BBC in my view clearly suffers from an extreme bias. This explains why so many people no longer trust its reporting.
I know from personal anecdotes from employees at the BBC that there is a kind of internal struggle going on to overcome the problem, but nobody I have yet spoken to denies that the organisation is ideologically captured. And we can all see it for ourselves. You might have seen the educational film by the BBC called Identity – Understanding Sexual and Gender Identities, aimed at 9 to 12 year-olds, which claimed that there are “over 100 gender identities”.
Where is the balance there? Why is the BBC making pseudo-religious proclamations to children as though they were uncontested fact?
[…]
But perhaps most damning of all is the question of the WPATH Files. In March of this year, a series of internal documents and videos from the World Professional Association for Transgender Health were leaked to journalist Michael Shellenberger. As Mia Hughes’s report for the Environmental Progress think tank revealed, these leaks showed that members of the world’s leading global authority in gender treatment were engaging in medical malpractice.
There are messages proving that surgeons and therapists are aware that a significant proportion of young people referred to gender clinicians suffer from mental health problems. They reveal that some specialists associated with WPATH are proceeding with treatment in the knowledge that no consent has been secured from either the children or those directly responsible for their wellbeing. They have also withheld from patients details of potential lifelong complications, or continued down this path knowing that the children do not understand the implications. And the WPATH Standards of Care are the go-to policies for gender treatment throughout the world, and have been influential in our own NHS.
[…]
And yet if you search for the WPATH Files on the BBC News website, what do you find? Precisely nothing.
May 22, 2024
The new queen of the AWFLs
Elizabeth Nickson on the rise of new NPR CEO, Katherine Maher:

Banner for Christopher Rufo’s article on Katherine Maher at City Journal.
https://christopherrufo.com/p/katherine-mahers-color-revolution
The polite world was fascinated last month when long-time NPR editor Uri Berliner confessed to the Stalinist suicide pact the public broadcaster, like all public broadcasters, seems to be on. Formerly it was a place of differing views, he claimed, but now it has sold as truth some genuine falsehoods like, for instance, the Russia hoax, after which it covered up the Hunter Biden laptop. And let’s not forget our censor-like behaviour regarding Covid and the vaccine. NPR bleated that they were still diverse in political opinion, but researchers found that all 87 reporters at NPR were Democrats. Berliner was immediately put on leave and a few days later resigned, no doubt under pressure.
Even more interesting was the reveal of the genesis of NPR’s new CEO, Katherine Maher, a 41-year-old with a distinctly odd CV. Maher had put in stints at a CIA cutout, the National Democratic Institute, and trotted onto the World Bank, UNICEF, the Council on Foreign Relations, the Center for Technology and Democracy, the Digital Public Library of America, and finally the famous disinfo site Wikipedia. That same week, Tunisia accused her of working for the CIA during the so-called Arab Spring. And, of course, she is a WEF young global leader.
She was marched out for a talk at the Carnegie Endowment where she was prayerfully interviewed and spouted mediatized language so anodyne, so meaningless, yet so filled with nods to her base the AWFULS (affluent white female urban liberals) one was amazed that she was able to get away with it. There was no acknowledgement that the criticism by this award-winning reporter/editor/producer, who had spent his life at NPR had any merit whatsoever, and in fact that he was wrong on every count. That this was a flagrant lie didn’t even ruffle her artfully disarranged short blonde hair.
Christopher Rufo did an intensive investigation of her career in City Journal. It is an instructive read and illustrative of a lot of peculiar yet stellar careers of American women. Working for Big Daddy is apparently something these ghastly creatures value. I strongly suggest reading Rufo’s piece linked here. It’s a riot of spooky confluences.
Intelligence has been embedded in media forever and a day. During my time at Time Magazine in London, the bureau chief, deputy bureau chief and no doubt the “war and diplomacy” correspondent all filed to Langley and each of them cruised social London ceaselessly for information. Tucker Carlson asserted on his interview with Aaron Rogers this week that intelligence operatives were laced through DC media and in fact, Mr. Watergate, Bob Woodward himself, had been naval intelligence a scant year before he cropped up at the Washington Post as “an intrepid fighter for the truth and freedom no matter where it led”. Watergate, of course, was yet another operation to bring down another inconvenient President; at this juncture, unless you are being puppeted by the CIA, you don’t get to stay in power. Refuse and bang bang or end up in court on insultingly stupid charges. As Carlson pointed out, all congressmen and senators are terrified by the security state, even and especially the ones on the intelligence committee who are supposed to be controlling them. They can install child porn on your laptop and you don’t even know it’s there until you are raided, said Carlson. The security state is that unethical, that power mad.
Now, it’s global. And feminine. Where is Norman Mailer when you need him?
May 2, 2024
When Malcolm Muggeridge investigated P.G. Wodehouse for MI6
Alan Ashworth explains the circumstances under which the great P.G. Wodehouse became the subject of an MI6 (Britain’s Secret Intelligence Service) treason investigation near the end of the Second World War:
[Malcolm Muggeridge:] “I first made Wodehouse’s acquaintance in circumstances which might have been expected to shake even his equanimity. This was in Paris just after the withdrawal of the German occupation forces. As Wodehouse well understood, the matter of his five broadcasts from Berlin would now have to be explained; and in the atmosphere of hysteria that war inevitably generates, the consequences might be very serious indeed. It would have been natural for him to be shaken, pale, nervous; on the contrary I found him calm and cheerful. I thought then, and think now more forcibly than ever, that this was due not so much to a clear conscience as to a state of innocence which mysteriously has survived in him.”
Muggeridge explains that he was attached to an MI6 contingent and a colleague “mentioned to me casually that he had received a short list of so-called traitors who cases needed to be investigated, one of the names being PG Wodehouse”. Muggeridge readily agreed to take on the case, “partly out of curiosity and partly from a feeling that no one who had made as elegant and original a contribution to the general gaiety of living should be allowed to get caught up in the larger buffooneries of war”. He duly visited Wodehouse at his hotel that same evening and the author described what had happened to him from the collapse in 1940 of France, where he was living with his wife Ethel, to his internment at a former lunatic asylum in Tost, Poland.
“The normal wartime procedure is to release civilian internees when they are sixty. Wodehouse was released some months before his sixtieth birthday as a result of well-meant representations by American friends – some resident in Berlin, America not being then at war with Germany. He made for Berlin, where his wife was awaiting him. The Berlin representative of the Columbia Broadcasting System asked him if he would like to broadcast to his American readers about his internment and foolishly he agreed, not realising the broadcasts would have to go over the German network and were bound to be exploited in the interest of Nazi propaganda.” [Here are German transcripts of the offending items.]
Muggeridge goes on: “It has been alleged that there was a bargain whereby Wodehouse agreed to broadcast in return for being released from Tost. This has frequently been denied and is, in fact, quite untrue but nonetheless still widely believed.”
Wodehouse came under virulent attack, particularly from Cassandra, the Daily Mirror columnist William Connor, who denounced him as a traitor to his country. Public libraries banned his books. Wodehouse wrote to the Home Secretary admitting he had been “criminally foolish” but said the broadcasts were “purely comic” and designed to show Americans a group of interned Englishmen keeping up their spirits. But the damage was done and the stigma stuck. After the war he spent the rest of his life in America.
In words that resonate half a century after their publication, Muggeridge says: “Lies, particularly in an age of mass communication, have much greater staying power than the truth.
“In the broadcasts there is not one phrase or word which can possibly be regarded as treasonable. Ironically enough, they were subsequently used at an American political warfare school as an example of how anti-German propaganda could subtly be put across by a skilful writer in the form of seemingly innocuous, light-hearted descriptive material. The fact is that Wodehouse is ill-fitted to live in an age of ideological conflict. He just does not react to human beings in that sort of way and never seems to hate anyone – not even old friends who turned on him. Of the various indignities heaped upon him at the time of his disgrace, the only one he really grieved over was being expunged from some alleged roll of honour at his old school, Dulwich.”
[…]
Muggeridge records that, when the war ended, the Wodehouses left France for America. “Ethel has been back to England several times but Wodehouse never, though he is always theoretically planning to come. I doubt if he ever will [he didn’t, dying in 1975 at the age of 93]. His attitude is like that of a man who has parted, in painful circumstances, from someone he loves and whom he both longs for and dreads to see again.”
April 7, 2024
Instructions for American Servicemen in Britain (1942)
Henry Getley on the US War Department publication Instructions for American Servicemen in Britain produced for incoming GIs on arrival in Britain from early in 1942:
[W]ith their troops pouring into this country from 1942 onwards to prepare for D-Day, officials at the US War Department did their best to make the culture clash as trouble-free as possible. One of their main efforts was issuing GIs with a seven-page foolscap leaflet called Instructions for American Servicemen in Britain.
It’s available in reprint as a booklet and makes fascinating reading, not least for its straightforward, jargon-free writing style and its overriding message – telling the Yanks to use “plain common horse sense” in their dealings with the British.
In parts, it now seems clumsy and condescending. But its purpose was praiseworthy – to try to get American troops to damp down the impression that they were overpaid, oversexed and over here. Many GIs qualified in all three aspects, of course, but you couldn’t blame the top brass for trying.
The leaflet paints a sympathetic (some would say patronising) picture for the incoming Americans of a Britain – “a small crowded island of forty-five million people” – that had been at war for three years, having initially stood alone against Hitler and braved the Blitz. Hence this “cradle of democracy” was now a “shop-worn and grimy” land of rationing, the blackout, shortages and austerity. But beneath the shabbiness, there was steel.
The British are tough. Don’t be misled by the British tendency to be soft-spoken and polite. If need be, they can be plenty tough. The English language didn’t spread across the oceans and over the mountains and jungles and swamps of the world because these people were panty-waists.
There were helpful hints about cricket, football, darts, pounds, shillings and pence, warm beer and badly-made coffee. And because we are two nations divided by a common language, the Yanks were urged to listen to the BBC.
In England the “upper crust” speak pretty much alike. You will hear the newscaster for the BBC (British Broadcasting Corporation). He is a good example, because he has been trained to talk with the “cultured” accent. He will drop the letter “r” (as people do in some sections of our own country) and will say “hyah” instead of “here”. He will use the broad “a”, pronouncing all the a’s in “banana” like the “a” in father.
However funny you may think this is, you will be able to understand people who talk this way and they will be able to understand you. And you will soon get over thinking it’s funny. You will have more difficulty with some of the local accents. It may comfort you to know that a farmer or villager from Cornwall very often can’t understand a farmer or villager in Yorkshire or Lancashire.
The GIs were warned against bravado and bragging, being told that the British were reserved but not unfriendly. “They will welcome you as friends and allies, but remember that crossing the ocean doesn’t automatically make you a hero. There are housewives in aprons and youngsters in knee pants in Britain who have lived through more high explosives in air raids than many soldiers saw in first-class barrages during the last war.”
February 27, 2024
Thank goodness we don’t get all the CBC we pay for!
In the dim, dark recesses of history … say twenty-five years ago … the CBC was what the government still seems to believe it is: a credible, trusted source of news and entertainment. In truth, it was never as loved as some might claim, as it had a deep bias in favour of Quebec and Ontario issues and tended to only occasionally remember the rest of the country. The federal government has been subsidizing the CBC, yet the network’s audience has shrunk to the point that it’s rare to encounter anyone who consumes very much of the programming on offer. Part of that is just the sheer variety of other options available to Canadians and part of it is the CBC’s sour, toxic, hectoring tone when lecturing about “the current thing”. Far from being a major player in upholding Canadian culture, the CBC is clearly one of the major factors that are destroying it:
… looking at the viewer and listener stats for the CBC, our national behemoth, which eats up $1.5 billion annually, and which amounts to 50% of the media dollars spent, is equally disheartening. The state spends another $600 million supporting once-successful media because “internet”. CBC television is watched by 3.9% of Canadians and only 0.8% watch CBC News. Again, half of all media dollars, half. Half is spent engaging less than 4% of Canadians. CBC radio is considered reasonably good, and is listened to by 10%, despite its vindictive calling out of anyone who disagrees with their hard socialist stance. As to other mainstream media, propped up by government via hundred of millions, it is still shedding staff and readers in double digits.
Despite every conceivable advantage, advertising on the CBC dropped 20% during the pandemic. In fact, they are so disliked that CBC is hiring “close protection security” for the next two years. They are so disliked, they have turned off commenting on their various programs. They are so disliked that there is a brand of coffee called “Defund the CBC”. This isn’t passive ignoring, this is active dislike to the point of needing bodyguards.
Why? Because our media show us to ourselves as racist, stupid, sexist, stupid, stupid and more stupid. And while they are at it, shallow and violent. That is the real reason, and the only reason CanCon is dying. They hate us. Why? The only people who have thrived during the past twenty years in Canada when private and public wealth doubled then doubled again, are the ones who live off the government, whether through mandated consulting in the enviro and other business, or direct granting or though quasi-private-sector jobs that are heavily subsidized. Public Private Partnerships have to be the most fiendish way to flat out loot the public ever been invented. Or straight up public sector jobs which are among the most lushly funded and unionized in the known universe, the number of which have grown 400% in the last ten years. Do or did you get six weeks of paid holiday a year?
And do they hate us, in fact correcting us is how they get the grants, the jobs, the subsidy. Everything they do is meant to fix us deplorable Canadians.
Sit at a downtown Toronto dinner party as I have, with say, the head of CBC drama, as I have and listen to just how much they hate the rest of Canada. Why? They hate the rest of Canada because they feel guilty. They know they are cheating and they know they are stealing. I tell ya, I needed close protection security — this woman was terrifying. “Sit Down While I’m Talking to You“, she roared at me.
December 8, 2023
The Real Betty Crocker’s Pineapple Upside Down Cake
Tasting History with Max Miller
Published 22 Aug 2023
(more…)
November 24, 2023
The Man Who Started the Cold War
World War Two
Published 23 Nov 2023What if I told you that a new conflict will sweep the globe in less than a year? It will open not with gunshots but with silent, shadowy espionage. The man who will kick off the Cold War is a quiet Canadian pilot, millionaire, and spymaster. A trusted aide to Churchill and FDR. I bet you haven’t heard this name before: William Stephenson.
(more…)
September 13, 2023
Why Do People In Old Movies Talk Weird?
BrainStuff – HowStuffWorks
Published 25 Nov 2014It’s not quite British, and it’s not quite American – so what gives? Why do all those actors of yesteryear have such a distinct and strange accent?
If you’ve ever heard old movies or newsreels from the thirties or forties, then you’ve probably heard that weird old-timey voice.
It sounds a little like a blend between American English and a form of British English. So what is this cadence, exactly?
This type of pronunciation is called the Transatlantic, or Mid-Atlantic, accent. And it isn’t like most other accents – instead of naturally evolving, the Transatlantic accent was acquired. This means that people in the United States were taught to speak in this voice. Historically Transatlantic speech was the hallmark of aristocratic America and theatre. In upper-class boarding schools across New England, students learned the Transatlantic accent as an international norm for communication, similar to the way posh British society used Received Pronunciation – essentially, the way the Queen and aristocrats are taught to speak.
It has several quasi-British elements, such a lack of rhoticity. This means that Mid-Atlantic speakers dropped their “r’s” at the end of words like “winner” or “clear”. They’ll also use softer, British vowels – “dahnce” instead of “dance”, for instance. Another thing that stands out is the emphasis on clipped, sharp t’s. In American English we often pronounce the “t” in words like “writer” and “water” as d’s. Transatlantic speakers will hit that T like it stole something. “Writer”. “Water”.
But, again, this speech pattern isn’t completely British, nor completely American. Instead, it’s a form of English that’s hard to place … and that’s part of why Hollywood loved it.
There’s also a theory that technological constraints helped Mid-Atlantic’s popularity. According to Professor Jay O’Berski, this nasally, clipped pronunciation is a vestige from the early days of radio. Receivers had very little bass technology at the time, and it was very difficult – if not impossible – to hear bass tones on your home device. Now we live in an age where bass technology booms from the trunks of cars across America.
So what happened to this accent? Linguist William Labov notes that Mid-Atlantic speech fell out of favor after World War II, as fewer teachers continued teaching the pronunciation to their students. That’s one of the reasons this speech sounds so “old-timey” to us today: when people learn it, they’re usually learning it for acting purposes, rather than for everyday use. However, we can still hear the effects of Mid-Atlantic speech in recordings of everyone from Katherine Hepburn to Franklin D. Roosevelt and, of course, countless films, newsreels and radio shows from the 30s and 40s.
(more…)
June 28, 2023
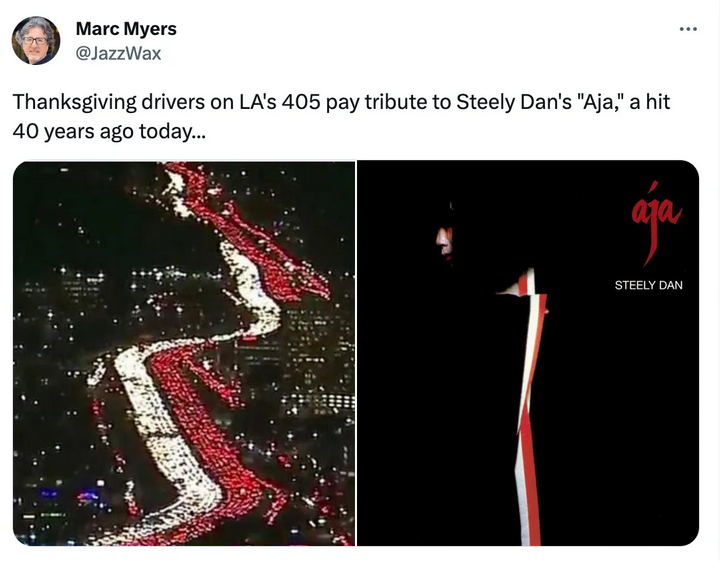
Ted Gioia’s confession – he’s a Dan stan
While I’ve never been much of a musicologist — and definitely not any kind of musician — I admit I had a very similar evolution of feeling toward the music of Steely Dan as Ted Gioia, who charts his progress from Never Dan to Dan stan:
I often make jokes about Steely Dan fans.
They’re bros and geeks and sad wannabes. But the painful truth is that I’m one of them now.
And if you don’t watch out, it could happen to you too.
At least I can laugh at myself. That’s good, because fans like me are the real target of the jokes.
And it’s true — we are a trifle obsessed.
If you’re a Dan stan, you see the band’s influence everywhere. Random patterns take on new Dan-esque shapes. For you it’s just rush hour traffic, but for us it’s a message from the cosmos.
But I wasn’t always like this. Once upon a time, I was a Steely Dan skeptic, a real Dan-o-phobe. I thought I was safe from their pernicious influence, but I was wrong.
This is my story.