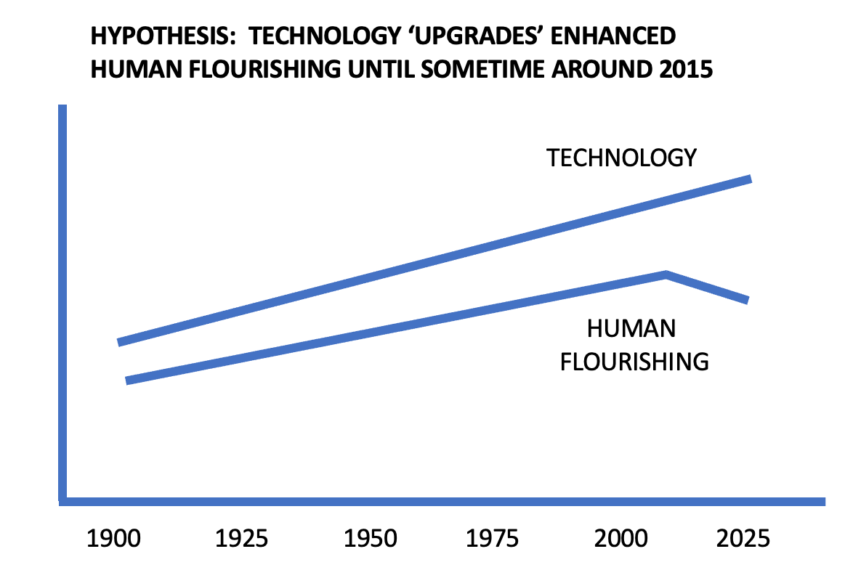
It may be hard to believe, but once upon a time we actually used to look forward to new technology releases and updated software. I know, I know, that’s asking you to believe fairy tales in our current “enshittification-as-a-service” technology dystopia. The Bone Writer — who worked in the same tech field that I once did — clearly understands why the promise of new technology has turned so negative:

Dead technology. Not because they’re broken, but because they’re no longer supported and THEREFORE no longer work.
I was straightening some stuff/junk up and came upon a pile of my e-Waste. It’s a damn shame that electronics devices are a planned obsolesce when they shouldn’t be. Especially the tablets and e-readers that would still work if the mothership, the corpo HQ, the evil Tech Bros, actually cared about their customers at all.
Do we need legislation that offers up some sort of tax write off incentive to get companies to support their shit for at least 10 years? I know what you’re saying … “That’s not a free market economy.” Yeah … well … The tech sector broke the free market economy a long time ago and now they actively hurt everyone with their greed and drive to force people into what comes next, every month to 3 months to 1 year.
That’s another reason prices never come down on tech stuff. They put out something new monthly to yearly, with just a small addition to the software or the design. Then they push it on people as if it is the BEST thing there ever was, creating FOMO. Then, some people will upgrade with every new device or software version sold.
[…]
Agile is the Devil’s Tool for Creating More Waste
Agile is the method that is used to push new software and updates out continuously. Get those updates out there and keep that device or software looking shiny but hold back the good stuff for the next big release. Even though the current iteration can likely support the next big release, we’re not going to do that. This way we can sell more shit to people and they will have FOMO so they will buy it up. Even though, the next big release isn’t all that great anyway… They consumer will eat it up.
Recycle It
The activist techies will just say, “Go ahead and recycle the old stuff.” As if it really gets recycled. More often than not (only 10% of recycled stuff actually gets recycled), it gets buried or sent to other countries to be disassembled and buried there, out of site. Both the tech sector and fashion industry are guilty of this. Meanwhile, YOU are told that if you recycle, you are doing your part to clean up the world, when you’re really just sending stuff elsewhere to pollute a third world country. Sleep easy though, it isn’t in YOUR backyard.