Bruce Schneier talks about the need to restore trust in government and the internet after all the proof we’ve had lately that “they” are lying to us pretty much all the time:
In July 2012, responding to allegations that the video-chat service Skype — owned by Microsoft — was changing its protocols to make it possible for the government to eavesdrop on users, Corporate Vice President Mark Gillett took to the company’s blog to deny it.
Turns out that wasn’t quite true.
Or at least he — or the company’s lawyers — carefully crafted a statement that could be defended as true while completely deceiving the reader. You see, Skype wasn’t changing its protocols to make it possible for the government to eavesdrop on users, because the government was already able to eavesdrop on users.
At a Senate hearing in March, Director of National Intelligence James Clapper assured the committee that his agency didn’t collect data on hundreds of millions of Americans. He was lying, too. He later defended his lie by inventing a new definition of the word “collect,” an excuse that didn’t even pass the laugh test.
As Edward Snowden’s documents reveal more about the NSA’s activities, it’s becoming clear that we can’t trust anything anyone official says about these programs.
Google and Facebook insist that the NSA has no “direct access” to their servers. Of course not; the smart way for the NSA to get all the data is through sniffers.
Apple says it’s never heard of PRISM. Of course not; that’s the internal name of the NSA database. Companies are publishing reports purporting to show how few requests for customer-data access they’ve received, a meaningless number when a single Verizon request can cover all of their customers. The Guardian reported that Microsoft secretly worked with the NSA to subvert the security of Outlook, something it carefully denies. Even President Obama’s justifications and denials are phrased with the intent that the listener will take his words very literally and not wonder what they really mean.
[…]
Ronald Reagan once said “trust but verify.” That works only if we can verify. In a world where everyone lies to us all the time, we have no choice but to trust blindly, and we have no reason to believe that anyone is worthy of blind trust. It’s no wonder that most people are ignoring the story; it’s just too much cognitive dissonance to try to cope with it.
This sort of thing can destroy our country. Trust is essential in our society. And if we can’t trust either our government or the corporations that have intimate access into so much of our lives, society suffers. Study after study demonstrates the value of living in a high-trust society and the costs of living in a low-trust one.

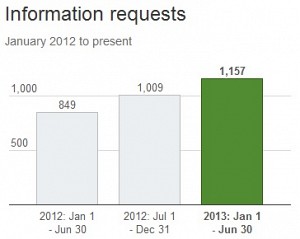 You know you’ve arrived as an online media operation when governments take an interest in who is speaking out, and make efforts to muzzle what’s published. That’s definitely the case with Twitter, the microblogging platform that started as an outlet for exhibitionist ADHD sufferers, only to become a powerful medium for sharing news and grassroots organizing. According to the company’s latest transparency report, governments around the world are issuing ever-more demands for information about the service’s users, and stepping up efforts to suppress tweeted content.
You know you’ve arrived as an online media operation when governments take an interest in who is speaking out, and make efforts to muzzle what’s published. That’s definitely the case with Twitter, the microblogging platform that started as an outlet for exhibitionist ADHD sufferers, only to become a powerful medium for sharing news and grassroots organizing. According to the company’s latest transparency report, governments around the world are issuing ever-more demands for information about the service’s users, and stepping up efforts to suppress tweeted content.