It’s been a year since the name Edward Snowden became known to the world, and it’s been a bumpy ride since then, as we found out that the tinfoil-hat-wearing anti-government conspiracy theorists were, if anything, under-estimating the actual level of organized, secret government surveillance. At The Register, Duncan Campbell takes us inside the “FIVE-EYED VAMPIRE SQUID of the internet”, the five-way intelligence-sharing partnership of US/UK/Canada/Australia/New Zealand:
One year after The Guardian opened up the trove of top secret American and British documents leaked by former National Security Agency (NSA) sysadmin Edward J Snowden, the world of data security and personal information safety has been turned on its head.
Everything about the safety of the internet as a common communication medium has been shown to be broken. As with the banking disasters of 2008, the crisis and damage created — not by Snowden and his helpers, but by the unregulated and unrestrained conduct the leaked documents have exposed — will last for years if not decades.
Compounding the problem is the covert network of subornment and control that agencies and collaborators working with the NSA are now revealed to have created in communications and computer security organisations and companies around the globe.
The NSA’s explicit objective is to weaken the security of the entire physical fabric of the net. One of its declared goals is to “shape the worldwide commercial cryptography market to make it more tractable to advanced cryptanalytic capabilities being developed by the NSA”, according to top secret documents provided by Snowden.
Profiling the global machinations of merchant bank Goldman Sachs in Rolling Stone in 2009, journalist Matt Taibbi famously characterized them as operating “everywhere … a great vampire squid wrapped around the face of humanity, relentlessly jamming its blood funnel into anything that smells like money”.
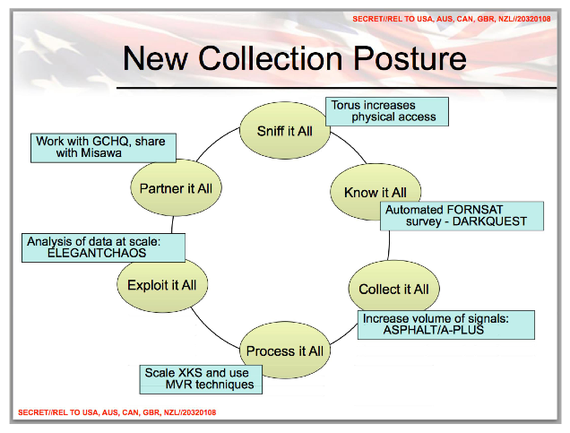
The NSA, with its English-speaking “Five Eyes” partners (the relevant agencies of the UK, USA, Australia, New Zealand and Canada) and a hitherto unknown secret network of corporate and government partners, has been revealed to be a similar creature. The Snowden documents chart communications funnels, taps, probes, “collection systems” and malware “implants” everywhere, jammed into data networks and tapped into cables or onto satellites.