Published on 3 Jul 2017
Encryption backdoors – breaking WhatsApp and iMessage’s security to let the government stop Bad Things – sounds like a reasonable idea. Here’s why it isn’t.
A transcript of this video’s available here: https://www.facebook.com/notes/tom-scott/why-the-government-shouldnt-break-whatsapp/1378434365572557/
August 12, 2017
Why The Government Shouldn’t Break WhatsApp
August 1, 2017
Ontario adopts voluntary self-surveillance app from CARROT Insights
I often joke about how inexpensive it appears to be to “influence” politicians, but it’s only fair to point out that the voters those easily influenced politicians represent are even more easy to influence:
Ontario announced earlier this month that it will become the fourth Canadian government to fund a behavioral modification application that rewards users for making “good choices” in regards to health, finance, and the environment. The Carrot Rewards smartphone app, which will receive $1.5 million from the Ontario government, credits users’ accounts with points toward the reward program of their choice in exchange for reaching step goals, taking quizzes and surveys, and engaging in government-approved messages.
The app, funded by the Canadian federal government and developed by Toronto-based company CARROT Insights in 2015, is sponsored by a number of companies offering reward points for their services as an incentive to “learn” how to improve wellness and budget finances. According to CARROT Insights, “All offers are designed by sources you can trust like the BC Ministry of Health, Newfoundland and Labrador Government, the Heart and Stroke Foundation, the Canadian Diabetes Association, and YMCA.” Users can choose to receive rewards for companies including SCENE, Aeroplan, Petro-Canada, or More Rewards, a loyalty program that partners with other businesses.
It’ll be interesting if they share the uptake of this new smartphone app … just how many of us are willing to let the government track just about all of our actions in exchange for “rewards”.
In order to use the app, users are giving Carrot Insights and the federal government permission to “access and collect information from your mobile device, including but not limited to, geo-location data, accelerometer/gyroscope data, your mobile device’s camera, microphone, contacts, calendar and Bluetooth connectivity in order to operate additional functionalities of the Services.”
Founder and CEO of CARROT Insights Andreas Souvaliotis launched the app in 2015 “with a focus on health but the company and its partner governments quickly realized it was effective at modifying behavior in other areas as well,” according to CTV News.
April 20, 2017
We now know that there are more than 30,000 registered gun owners in London
What’s disturbing about the knowledge is that London’s Metropolitan Police revealed that information to a private company and may have violated British privacy laws in the process:
London gun owners are asking questions of the Metropolitan Police after the force seemingly handed the addresses of 30,000 firearm and shotgun owners to a direct mail marketing agency for a commercial firm’s advertising campaign.
The first any of the affected people knew about the blunder was when the leaflet (pictured below) landed on their doormats in Tuesday’s post.
Titled “Protect your firearms and shotguns with Smartwater”, the leaflet – which features Met Police logos – advises firearm and shotgun certificate holders to “buy a firearms protection pack at a reduced price” of £8.95.
Smartwater is basically invisible ink. You mark your property using it and if you are burgled, police can use a UV light reader to see who rightfully owns stolen items. The company behind it was formed by an ex-police detective and his industrial chemist brother, and the firm has since forged very close links with a number of UK police forces. Its website boasts of the “traceable liquid’s” crime-reducing properties, something that police actively endorse.
[…]
The front and reverse of the Metropolitan Police Smartwater firearms leaflet
Questions were immediately raised as to whether the Met had broken the law. The data protection statement that both police and certificate holders agree to is found in Firearms Form 201 (PDF), the application form for a firearm certificate. It says:
I understand that all information submitted will be handled in accordance with the Data Protection Act 1998 and the Freedom of Information Act 2000 and connected legislation. I understand and give consent for information contained within my application form or obtained in the course of deciding the application to be shared with: my GP, other government departments, regulatory bodies or enforcement agencies in the course of either deciding the application or in pursuance of maintaining public safety or the peace.
Note: Any information shared will be shared in accordance with data sharing protocols. We do not share your personal or company details with other applicants or members of the public and treat information in connection with the application in confidence, but individuals should be aware that we may be required to disclose some information in accordance with the legislation referred to above.
The Register has made the Information Commissioner’s Office aware of the breach and is awaiting a statement from the data watchdog.
April 16, 2017
If Walls Could Talk The History of the Home Episode 3 The Bedroom
Published on 1 Feb 2017
March 31, 2017
“You can’t buy my internet data. You can’t buy your internet data. That’s not how this works“
At Techdirt, Mike Masnick bravely attempts to tamp down the hysteria over this week’s vote in Congress to kill broadband privacy protections (which, as he notes, hadn’t yet come into effect anyway):
People are rightfully angry and upset about this. The privacy protections were fairly simple, and would have been helpful in stopping truly egregious behavior by some dominant ISPs who have few competitors, and thus little reason to treat people right. But misleading and misinforming people isn’t helpful either.
[…]
But here’s the real problem: you can’t buy Congress’ internet data. You can’t buy my internet data. You can’t buy your internet data. That’s not how this works. It’s a common misconception. We even saw this in Congress four years ago, where Rep. Louis Gohmert went on a smug but totally ignorant rant, asking why Google won’t sell the government all the data it has on people. As we explained at the time, that’s not how it works*. Advertisers aren’t buying your browsing data, and ISPs and other internet companies aren’t selling your data in a neat little package. It doesn’t help anyone to blatantly misrepresent what’s going on.
When ISPs or online services have your data and “sell” it, it doesn’t mean that you can go to, say, AT&T and offer to buy “all of Louis Gohmert’s browsing history.” Instead, what happens is that these companies collect that data for themselves and then sell targeting. That is, when Gohmert goes to visit his favorite publication, that website will cast out to various marketplaces for bids on what ads to show. Thanks to information tracking, it may throw up some demographic and interest data to the marketplace. So, it may say that it has a page being viewed by a male from Texas, who was recently visiting webpages about boardgames and cow farming (to randomly choose some items). Then, from that marketplace, some advertisers’ computerized algorithms will more or less say “well, I’m selling boardgames about cows in Texas, and therefore, this person’s attention is worth 1/10th of a penny more to me than some other company that’s selling boardgames about moose.” And then the webpage will display the ad about cow boardgames. All this happens in a split second, before the page has fully loaded.
At no point does the ad exchange or any of the advertisers know that this is “Louis Gohmert, Congressional Rep.” Nor do they get any other info. They just know that if they are willing to spend the required amount to get the ad shown via the marketplace bidding mechanism, it will show up in front of someone who is somewhat more likely to be interested in the content.
That’s it.
* Amusingly, Rep. Gohmert voted to repeal the privacy protections, which makes no sense if he actually believed what he was saying in that hearing a few years ago…
H/T to Amy Alkon for the link.
On a related note, LifeHacker posted a recommendation for “The Laziest, Cheapest Way to Circumvent Your Snooping ISP“. (Spoiler: it’s Opera). I use Opera, but not exclusively … I also use Brave, Chrome, and Firefox on a daily basis.
March 11, 2017
The EFF’s guide to digital privacy at US border crossings
The Electronic Frontier Foundation (EFF) provides a quick overview of your rights when entering the United States:
February 23, 2017
November 6, 2016
Canadian intelligence agencies and domestic overreach
Michael Geist on the drumbeat of revelations — but less outrage than you’d expect — on the extent of surveillance being conducted within Canada by CSIS and law enforcement organizations:
In the aftermath of the Snowden revelations in which the public has become largely numb to new surveillance disclosures, the Canadian reports over the past week will still leave many shocked and appalled. It started with the Ontario Provincial Police mass text messaging thousands of people based on cellphone usage from nearly a year earlier (which is not government surveillance per se but highlights massive geo-location data collection by telecom carriers and extraordinary data retention periods), continued with the deeply disturbing reports of surveillance of journalists in Quebec (which few believe is limited to just Quebec) and culminated in yesterday’s federal court decision that disclosed that CSIS no longer needs warrants for tax records (due to Bill C-51) and took the service to task for misleading the court and violating the law for years on its metadata collection and retention program.
The ruling reveals a level of deception that should eliminate any doubts that the current oversight framework is wholly inadequate and raises questions about Canadian authorities commitment to operating within the law. The court found a breach of a “duty of candour” (which most people would typically call deception or lying) and raises the possibility of a future contempt of court proceeding. While CSIS attempted to downplay the concern by noting that the data collection in question – metadata involving a wide range of information used in a massive data analysis program – was collected under a court order, simply put, the court found that the retention of the data was illegal. Further, the amount of data collection continues to grow (the court states the “scope and volume of incidentally gathered information has been tremendously enlarged”), leading to the retention of metadata that is not part of an active investigation but rather involves non-threat, third party information. In other words, it is precisely the massive, big data metadata analysis program feared by many Canadians.
The court ruling comes after the Security Intelligence Review Committee raised concerned about CSIS bulk data collection in its latest report and recommended that that inform the federal court about the activities. CSIS rejected the recommendation. In fact, the court only became aware of the metadata retention due to the SIRC report and was astonished by the CSIS response, stating that it “shows a worrisome lack of understanding of, or respect for, the responsibilities of a party [SIRC] benefiting from the opportunity to appear ex parte.”
July 27, 2016
Security concerns with the “Internet of things”
When it comes to computer security, you should always listen to what Bruce Schneier has to say, especially when it comes to the “Internet of things”:
Classic information security is a triad: confidentiality, integrity, and availability. You’ll see it called “CIA,” which admittedly is confusing in the context of national security. But basically, the three things I can do with your data are steal it (confidentiality), modify it (integrity), or prevent you from getting it (availability).
So far, internet threats have largely been about confidentiality. These can be expensive; one survey estimated that data breaches cost an average of $3.8 million each. They can be embarrassing, as in the theft of celebrity photos from Apple’s iCloud in 2014 or the Ashley Madison breach in 2015. They can be damaging, as when the government of North Korea stole tens of thousands of internal documents from Sony or when hackers stole data about 83 million customer accounts from JPMorgan Chase, both in 2014. They can even affect national security, as in the case of the Office of Personnel Management data breach by — presumptively — China in 2015.
On the Internet of Things, integrity and availability threats are much worse than confidentiality threats. It’s one thing if your smart door lock can be eavesdropped upon to know who is home. It’s another thing entirely if it can be hacked to allow a burglar to open the door — or prevent you from opening your door. A hacker who can deny you control of your car, or take over control, is much more dangerous than one who can eavesdrop on your conversations or track your car’s location.
With the advent of the Internet of Things and cyber-physical systems in general, we’ve given the internet hands and feet: the ability to directly affect the physical world. What used to be attacks against data and information have become attacks against flesh, steel, and concrete.
Today’s threats include hackers crashing airplanes by hacking into computer networks, and remotely disabling cars, either when they’re turned off and parked or while they’re speeding down the highway. We’re worried about manipulated counts from electronic voting machines, frozen water pipes through hacked thermostats, and remote murder through hacked medical devices. The possibilities are pretty literally endless. The Internet of Things will allow for attacks we can’t even imagine.
The increased risks come from three things: software control of systems, interconnections between systems, and automatic or autonomous systems. Let’s look at them in turn
I’m usually a pretty tech-positive person, but I actively avoid anything that bills itself as being IoT-enabled … call me paranoid, but I don’t want to hand over local control of my environment, my heating or cooling system, or pretty much anything else on my property to an outside agency (whether government or corporate).
March 29, 2016
Why did Apple suddenly grow a pair over consumer privacy and (some) civil rights?
Charles Stross has a theory:
A lot of people are watching the spectacle of Apple vs. the FBI and the Homeland Security Theatre and rubbing their eyes, wondering why Apple (in the person of CEO Tim Cook) is suddenly the knight in shining armour on the side of consumer privacy and civil rights. Apple, after all, is a goliath-sized corporate behemoth with the second largest market cap in US stock market history — what’s in it for them?
As is always the case, to understand why Apple has become so fanatical about customer privacy over the past five years that they’re taking on the US government, you need to follow the money.
[…]
Apple see their long term future as including a global secure payments infrastructure that takes over the role of Visa and Mastercard’s networks — and ultimately of spawning a retail banking subsidiary to provide financial services directly, backed by some of their cash stockpile.
The FBI thought they were asking for a way to unlock a mobile phone, because the FBI is myopically focussed on past criminal investigations, not the future of the technology industry, and the FBI did not understand that they were actually asking for a way to tracelessly unlock and mess with every ATM and credit card on the planet circa 2030 (if not via Apple, then via the other phone OSs, once the festering security fleapit that is Android wakes up and smells the money).
If the FBI get what they want, then the back door will be installed and the next-generation payments infrastructure will be just as prone to fraud as the last-generation card infrastructure, with its card skimmers and identity theft.
And this is why Tim Cook is willing to go to the mattresses with the US department of justice over iOS security: if nobody trusts their iPhone, nobody will be willing to trust the next-generation Apple Bank, and Apple is going to lose their best option for securing their cash pile as it climbs towards the stratosphere.
March 20, 2016
Apple software engineers threaten to quit rather than crack encryption for the government
It’s only a rumour rather than a definite stand, but it is a hopeful one for civil liberties:
The spirit of anarchy and anti-establishment still runs strong at Apple. Rather than comply with the government’s requests to develop a so-called “GovtOS” to unlock the iPhone 5c of San Bernardino shooter Syed Rizwan Farook, The New York Times‘ half-dozen sources say that some software engineers may quit instead. “It’s an independent culture and a rebellious one,” former Apple engineering manager Jean-Louis Gassée tells NYT. “If the government tries to compel testimony or action from these engineers, good luck with that.”
Former senior product manager for Apple’s security and privacy division Window Snyder agrees. “If someone attempts to force them to work on something that’s outside their personal values, they can expect to find a position that’s a better fit somewhere else.”
In another instance of Apple’s company culture clashing with what the federal government demands, the development teams are apparently relatively siloed off from one another. It isn’t until a product gets closer to release that disparate teams like hardware and software engineers come together for finalizing a given gizmo. NYT notes that the team of six to 10 engineers needed to develop the back door doesn’t currently exist and that forcing any sort of collaboration would be incredibly difficult, again, due to how Apple works internally.
January 31, 2016
“To be honest, the spooks love PGP”
If nothing else, it’s a needle in their acres of data haystacks. Use of any kind of encryption doesn’t necessarily let CSIS and their foreign friends read your communications, but it alerts them that you think you’ve got something to say that they shouldn’t read:
Although the cops and Feds wont stop banging on and on about encryption – the spies have a different take on the use of crypto.
To be brutally blunt, they love it. Why? Because using detectable encryption technology like PGP, Tor, VPNs and so on, lights you up on the intelligence agencies’ dashboards. Agents and analysts don’t even have to see the contents of the communications – the metadata is enough for g-men to start making your life difficult.
“To be honest, the spooks love PGP,” Nicholas Weaver, a researcher at the International Computer Science Institute, told the Usenix Enigma conference in San Francisco on Wednesdy. “It’s really chatty and it gives them a lot of metadata and communication records. PGP is the NSA’s friend.”
Weaver, who has spent much of the last decade investigating NSA techniques, said that all PGP traffic, including who sent it and to whom, is automatically stored and backed up onto tape. This can then be searched as needed when matched with other surveillance data.
Given that the NSA has taps on almost all of the internet’s major trunk routes, the PGP records can be incredibly useful. It’s a simple matter to build a script that can identify one PGP user and then track all their contacts to build a journal of their activities.
Even better is the Mujahedeen Secrets encryption system, which was released by the Global Islamic Media Front to allow Al Qaeda supporters to communicate in private. Weaver said that not only was it even harder to use than PGP, but it was a boon for metadata – since almost anyone using it identified themselves as a potential terrorist.
“It’s brilliant!” enthused Weaver. “Whoever it was at the NSA or GCHQ who invented it give them a big Christmas bonus.”
January 7, 2016
QotD: The right to record police officers
Some advice for the beleaguered and backward states of Illinois, Massachusetts, et al.: If police are not obliged to ask our permission before recording their public encounters with us, then we should not be obliged to ask their permission before recording our public encounters with them. That states generally dominated by so-called progressives should be so insistent upon asymmetric police powers and special privileges for government’s armed agents is surprising only to those who do not understand the basic but seldom-spoken truth about progressivism: The welfare state is the police state.
Why Illinois Republicans are on board is another matter, bringing up the eternal question that conservatives can expect to be revisiting frequently after January: What, exactly, is the point of the Republican party?
Illinois is attempting to resurrect what the state’s politicians pretend is a privacy-protecting anti-surveillance law; in reality, it is the nearly identical reincarnation of the state’s earlier anti-recording law, the main purpose of which was to charge people who record police encounters with a felony, an obvious and heavy-handed means of discouraging such recording. Illinois’s state supreme court threw the law out on the grounds that police do not have a reasonable expectation of privacy when carrying out their duties, though police and politicians argued the contrary — apparently, some part of the meaning of the phrase “public servants” eludes them. The new/old law is, by design, maddeningly vague, and will leave Illinois residents unsure of which encounters may be legally recorded and which may not.
Here is the solution: Pass a law explicitly recognizing the right of citizens to record police officers. It is important to note that such a law would recognize a right rather than create one: Government has no legitimate power to forbid free people from using cameras, audio-recording devices, or telephones in public to document the business of government employees. The statute would only clarify that Americans — even in Illinois — already are entitled to that right.
Kevin D. Williamson, “Prairie State Police State”, National Review, 2014-12-10.
December 4, 2015
QotD: “Dance like nobody’s watching”
I always laugh when I hear the phrase, “Dance like nobody’s watching.” It’s 2015. Everybody’s watching.
Jim Treacher, “Mac & Cheese Dude Is Sorry For Being An [Incredibly Unpleasant Person]”, The Daily Caller, 2015-10-13.
November 23, 2015
Do you have a smartphone? Do you watch TV? You might want to reconsider that combination
At The Register, Iain Thomson explains a new sneaky way for unscrupulous companies to snag your personal data without your knowledge or consent:
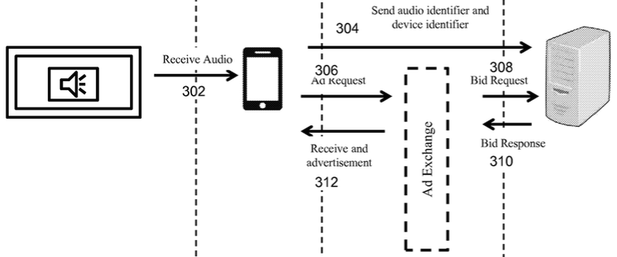
Earlier this week the Center for Democracy and Technology (CDT) warned that an Indian firm called SilverPush has technology that allows adverts to ping inaudible commands to smartphones and tablets.
Now someone has reverse-engineered the code and published it for everyone to check.
SilverPush’s software kit can be baked into apps, and is designed to pick up near-ultrasonic sounds embedded in, say, a TV, radio or web browser advert. These signals, in the range of 18kHz to 19.95kHz, are too high pitched for most humans to hear, but can be decoded by software.
An application that uses SilverPush’s code can pick up these messages from the phone or tablet’s builtin microphone, and be directed to send information such as the handheld’s IMEI number, location, operating system version, and potentially the identity of the owner, to the application’s backend servers.
Imagine sitting in front of the telly with your smartphone nearby. An advert comes on during the show you’re watching, and it has a SilverPush ultrasonic message embedded in it. This is picked up by an app on your mobile, which pings a media network with information about you, and could even display followup ads and links on your handheld.
“This kind of technology is fundamentally surreptitious in that it doesn’t require consent; if it did require it then the number of users would drop,” Joe Hall, chief technologist at CDT told The Register on Thursday. “It lacks the ability to have consumers say that they don’t want this and not be associated by the software.”
Hall pointed out that very few of the applications that include the SilverPush SDK tell users about it, so there was no informed consent. This makes such software technically illegal in Europe and possibly in the US.