David Gewirtz says that the press has totally mis-reported the scale of government security breaches:
Summary: This is one of those articles that spoils your faith in mankind. Not only are government security incidents fully into holy-cow territory, the press is reporting numbers three magnitudes too low because someone misread a chart and everyone else copied that report.
You might think this was an April Fool’s gag, except it was published on April 2nd, not April 1st.
According to testimony given by Gregory C. Wilshusen [PDF], Director of Information Security Issues for the Government Accountability Office to United States Senate Committee on Homeland Security and Governmental Affairs that, and I quote, “most major federal agencies had weaknesses in major categories of information security controls.”
In other words, some government agency data security functions more like a sieve than a lockbox.
Some of the data the GAO presented was deeply disturbing. For example, the number of successful breaches doubled since 2009. Doubled. There’s also a story inside this story, which I’ll discuss later in the article. Almost all of the press reporting on this testimony got the magnitude of the breach wrong. Most reported that government security incidents numbered in the thousands, when, in fact, they numbered in the millions.
Emphasis mine. Here are the actual numbers:
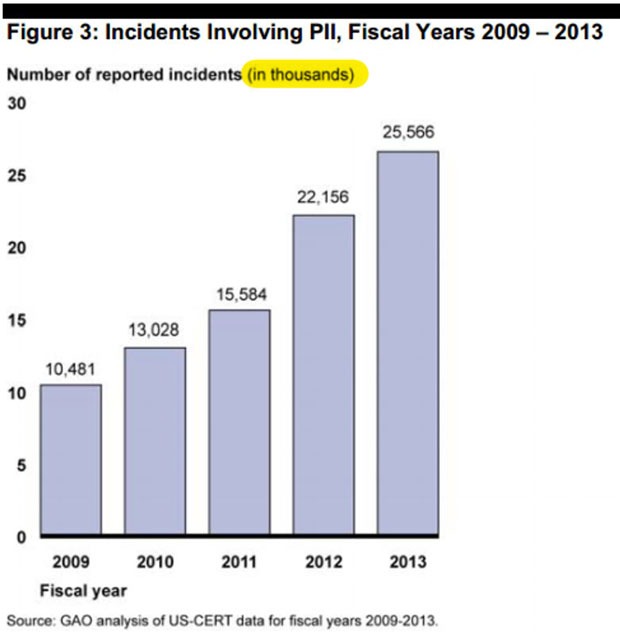
Incidents involving personal identifying information grew from about 10.5 million in 2009 to over 25 million last year. By the way, some press reports on this misread the GAO’s charts. For example, the Washington Free Beacon wrote about this, claiming “25,566 incidents of lost taxpayer data, Social Security numbers, patient health information.” What they missed was the little notation on the chart that says “in thousands,” so when they reported 25,566 incidents, what that really reads as is 25,566 x 1000 incidents.
This is an example of how the Internet echo chamber can get information very, very wrong. The Chicago Tribune, via Reuters reported the same incorrect statistic. So did InformationWeek. So did FierceHealthIT. Business Insider picked up the Reuters report and happily repeated the same statistic — which was three orders of magnitude incorrect.
This is why I always try to go to the original source material [PDF] and not just repeat the crap other writers are parroting. It’s more work, but it means the difference between reporting 25 thousand government breaches and 25 million government breaches. 25 thousand is disturbing. 25 million is horrifying.