Andrew Coyne on cryptocurrencies:

“Bitcoin – from WSJ”by MarkGregory007 is licensed under CC BY-NC-SA 2.0
Sign of the times: the convenience store in my block of mid-town Toronto has installed, in addition to the usual fare of milk, cigarettes and magazines, an ATM dispensing bitcoins. Customers insert their debit cards and buy bitcoin, which they can then use to … to …
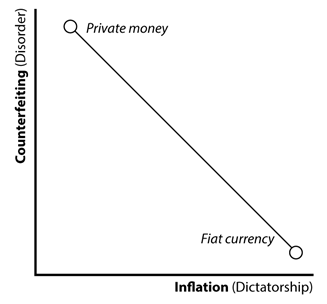
To do what, exactly, that they could not do with regular money? Bitcoin, the original cryptocurrency — there are now dozens of competitors — has always struck me as a solution in search of a problem. Its chief selling point, the anonymity made possible by its system of ultra-encrypted peer-to-peer transactions, unmediated by the banking system and beyond reach of the regulators, would seem of most appeal to two groups: crooks and cranks.
Oh, and a third: speculators. The price of cryptocurrencies has tended to fluctuate wildly — having fallen to a third of its peak against the U.S. dollar last year, Bitcoin has tripled in value so far in 2019. Cryptocurrencies are unlikely to achieve widespread use as mediums of exchange so long as they fail to fulfil one of money’s other primary functions, as stores of value.
The Wild West reputation the privately issued currencies have acquired — one of the most popular, Dogecoin, was invented by a 26-year-old Australian in 2013 as a joke — will be one of the early hurdles confronting Facebook’s recent entry into the field. The company hopes its 2.4 billion users will soon be buying goods and services from each other with Libra, as the proposed digital currency is called, wherever on earth either party may happen to be.
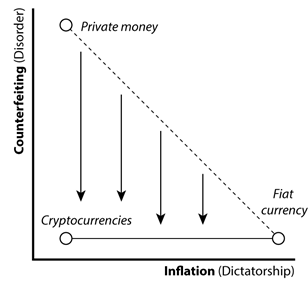
And yet Libra differs from Bitcoin and its ilk in several important ways. One, while it makes use of the same blockchain encryption technology as Bitcoin to ensure the security of payments, it is not based on the same anarchic premise.
In contrast to Bitcoin’s unsupervised, massively distributed, “permissionless” network, Libra will operate, at least initially, via Facebook’s Messenger and WhatsApp platforms, which are very much subject to its control. The company, and the others it has recruited as partners — names like Visa, Mastercard, and PayPal — are likewise highly visible targets of regulatory oversight, and indeed have signalled they intend to work with national banking regulators.