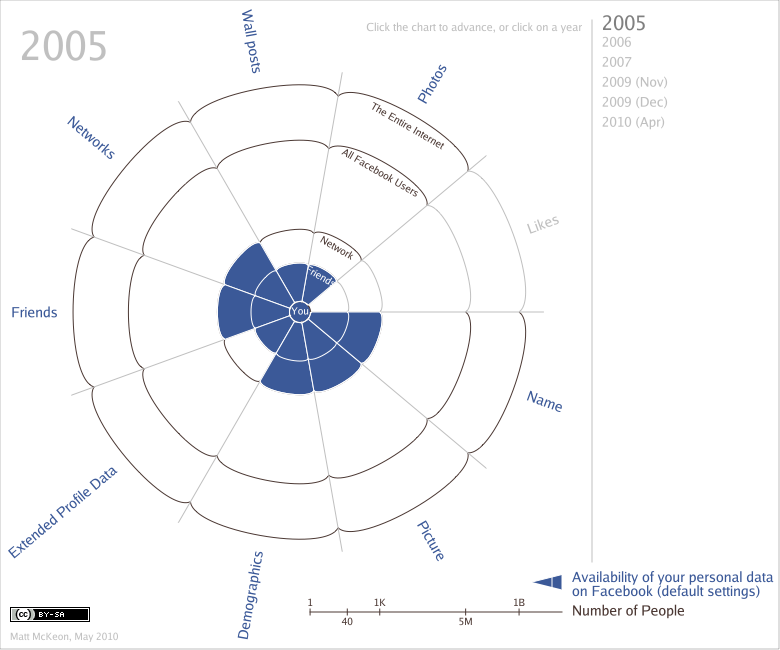
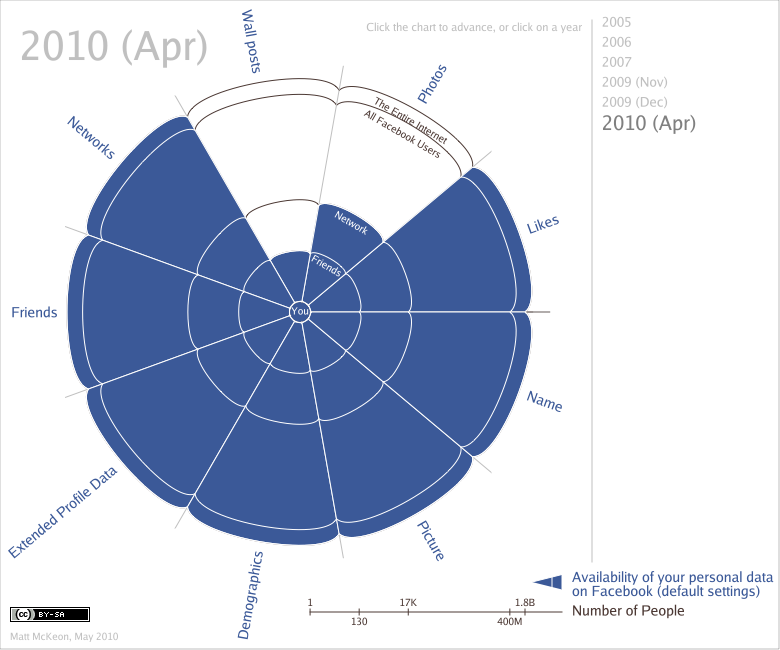
Julian Assange talked to Forbes about the next big WikiLeaks release of confidential data:
Early next year, Julian Assange says, a major American bank will suddenly find itself turned inside out. Tens of thousands of its internal documents will be exposed on Wikileaks.org with no polite requests for executives’ response or other forewarnings. The data dump will lay bare the finance firm’s secrets on the Web for every customer, every competitor, every regulator to examine and pass judgment on.
When? Which bank? What documents? Cagey as always, Assange won’t say, so his claim is impossible to verify. But he has always followed through on his threats. Sitting for a rare interview in a London garden flat on a rainy November day, he compares what he is ready to unleash to the damning e-mails that poured out of the Enron trial: a comprehensive vivisection of corporate bad behavior. “You could call it the ecosystem of corruption,” he says, refusing to characterize the coming release in more detail. “But it’s also all the regular decision making that turns a blind eye to and supports unethical practices: the oversight that’s not done, the priorities of executives, how they think they’re fulfilling their own self-interest.”