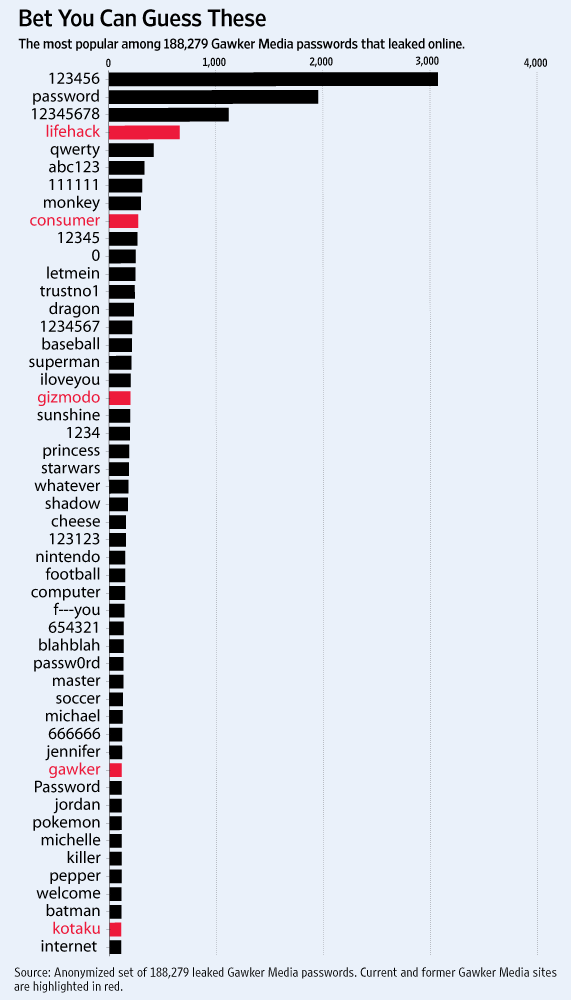
There’s been a short cycle of “we’re running out of internet addresses” articles over the last few months, as the available free blocks of IPv4 addresses are allocated. By now, we were all theoretically supposed to have moved on to the successor addressing scheme, IPv6:
On the 8 June, it’ll be World IPv6 Day — a coordinated effort by major services on the internet, including Google and Facebook, to provide their services using the new version of the Internet Protocol. It’s part of the plans to cope with internet addresses ‘running out’. But just what is IPv6 — and what does it mean for most users?
At its most simple, IPv6 is the successor to IPv4 which has become the de facto standard for both local and global connectivity. It includes many extra features, including processing speed-ups, and enhancements to security and to quality of service, but the one that’s really driving the need to change is that there are many more internet addresses available with IPv6.
Most Reg Hardware readers will be familiar with the look of an IPv4 address: it’s 32 bits long, and typically written as a series of four eight-bit decimal numbers, separated by full stops, like 10.0.0.1.
An IPv6 address is 128 bits long, and usually represented by groups of four hexadecimal digits, separated by colons. Each of those four digits represents 16 bits, so there are up to eight groups, giving IPv6 addresses that look like 2001:0470:1f09:1890:021f:f3ff:fe51:43f8.
It won’t be a simple case of turning on IPv6 and turning off IPv4, however, as there’s still huge numbers of devices that depend on IPv4. Over time, more and more devices (not just computers, or not only what we tend to think of as “computers”) will work natively with IPv6 addresses.
You won’t just get a single IPv4 address from your ISP anymore: you’ll get a huge block of addresses (“you’ll receive more addresses for your home network [than the] whole of the IPv4 internet”).
Typically, a broadband customer will be given a set of IPv6 addresses for their network, and the router will also provide an IPv4 address and NAT (Network Address Translation) for devices that can’t use the new protocol. The big change for many people is that all their IPv6 devices will be publicly available to the net. That will make setting up many devices much simpler, but also reinforces the need for a proper firewall in the router.

 The N-Mark standard defines an embedded tag, which can communicate and provide encrypted authentication using power induced by the reader – such a tag can therefore be embedded in a credit card or key fob without needing its own power supply.
The N-Mark standard defines an embedded tag, which can communicate and provide encrypted authentication using power induced by the reader – such a tag can therefore be embedded in a credit card or key fob without needing its own power supply. A Brazilian Christian sect has allegedly sought to exorcise the Universal Serial Bus (USB) because its symbol resembles a pitchfork, favoured sinner-spiking implement of one Old Nick, esq.
A Brazilian Christian sect has allegedly sought to exorcise the Universal Serial Bus (USB) because its symbol resembles a pitchfork, favoured sinner-spiking implement of one Old Nick, esq.