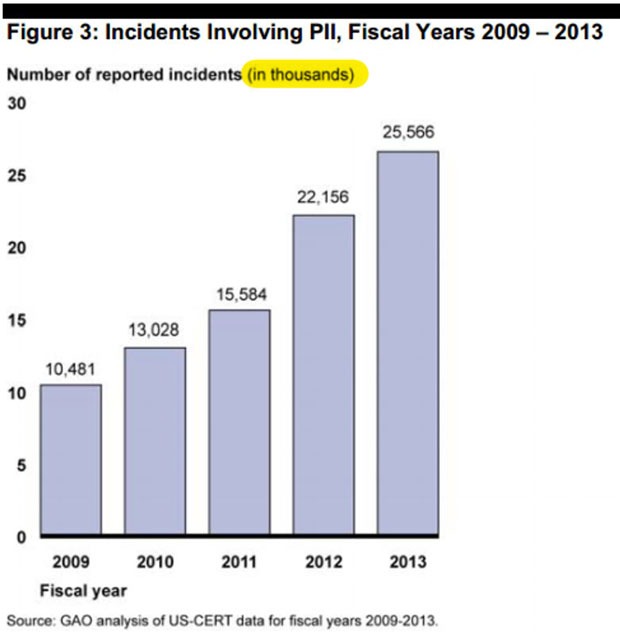
At Techdirt, Tim Cushing relives that brief, shining moment when the nation seemed to suddenly notice — and care about — the ongoing militarization of the police:
It’s an idea that almost makes sense, provided you don’t examine it too closely. America’s neverending series of intervention actions and pseudo-wars has created a wealth of military surplus — some outdated, some merely more than what was needed. Rather than simply scrap the merchandise or offload it at cut-rate prices to other countries’ militaries (and face the not-unheard-of possibility that those same weapons/vehicles might be used against us), the US government decided to distribute it to those fighting the war (on drugs, mostly) at home: law enforcement agencies.
What could possibly go wrong?
Well, it quickly became a way to turn police departments into low-rent military operations. Law enforcement officials sold fear and bought assault rifles, tear gas, grenade launchers and armored vehicles. They painted vivid pictures of well-armed drug cabals and terrorists, both domestic and otherwise, steadily encroaching on the everyday lives of the public, outmanning and outgunning the servers and protectors.
It worked. The Department of Homeland Security was so flattered by the parroting of its terrorist/domestic extremist talking points that it handed out generous grants and ignored incongruities, like a town of 23,000 requesting an armored BearCat because its annual Pumpkinfest might be a terrorist target.
Then the Ferguson protests began after Michael Brown’s shooting in August, and the media was suddenly awash in images of camouflage-clad cops riding armored vehicles while pointing weapons at protesters, looking for all the world like martial law had been declared and the military had arrived to quell dissent and maintain control.
This prompted a discussion that actually reached the halls of Congress. For a brief moment, it looked like there might be a unified movement to overhaul the mostly-uncontrolled military equipment re-gifting program. But now that the indictment has been denied and the city of Ferguson is looted and burning, those concerns appear to have been forgotten.

 I actually chuckled when I read rumor that the few anti-open-source advocates still standing were crowing about the Heartbleed bug, because I’ve seen this movie before after every serious security flap in an open-source tool. The script, which includes a bunch of people indignantly exclaiming that many-eyeballs is useless because bug X lurked in a dusty corner for Y months, is so predictable that I can anticipate a lot of the lines.
I actually chuckled when I read rumor that the few anti-open-source advocates still standing were crowing about the Heartbleed bug, because I’ve seen this movie before after every serious security flap in an open-source tool. The script, which includes a bunch of people indignantly exclaiming that many-eyeballs is useless because bug X lurked in a dusty corner for Y months, is so predictable that I can anticipate a lot of the lines.