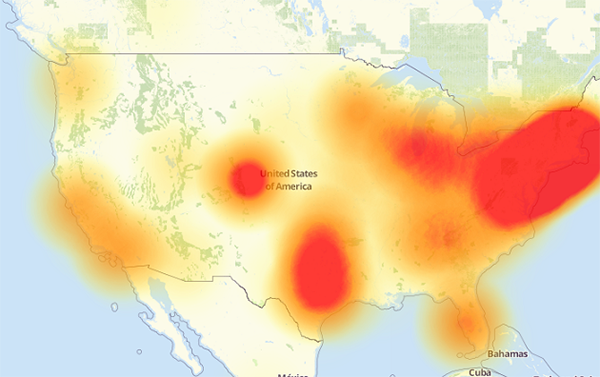
Bruce Schneier believes it will take government action (or as The Register phrased it, “Uncle Sam … putting boots to asses”) to get any significant improvement in Internet-of-Shit device security:
Any sort of lasting security standard in IoT devices may only happen if governments start doling out stiff penalties.
So said author and computer security guru Bruce Schneier, who argued during a panel discussion at the Aspen Cyber Summit this week that without regulation, there is little hope the companies hooking their products up to the internet will implement proper security protections.
“Looking at every other industry, we don’t get security unless it is done by the government,” Schneier said.
“I challenge you to find an industry in the last 100 years that has improved security without being told [to do so] by the government.”
Schneier went on to point out that, as it stands, companies have little reason to implement safeguards into their products, while consumers aren’t interested in reading up about appliance vendors’ security policies.
“I don’t think it is going to be the market,” Schneier argued. “I don’t think people are going to say I’m going to choose my refrigerator based on the number of unwanted features that are in the device.”
Schneier is not alone in his assessment either. Fellow panellist Johnson & Johnson CISO Marene Allison noted that manufacturers have nothing akin to a bill of materials for their IP stacks, so even if customers want to know how their products and data are secured, they’re left in the dark.
“Most of the stuff out there, even as a security professional, I have to ask myself, what do they mean?” Allison said.