SplashData's Top 100 Worst Passwords of 2018 from John Hall on Vimeo.
January 4, 2019
SplashData’s Top 100 Worst Passwords of 2018
May 5, 2018
Passwords, again
At The Register, a meditation on passwords by Kieren McCarthy:
“It’s World #PasswordDay! A reminder to change your pins/passwords frequently,” it advised anyone following the hashtag “PasswordDay”. But this, as lots of people quickly pointed out, is terrible advice.
But hang on a second: isn’t that the correct advice? Weren’t all sysadmins basically forced to change their systems to make people reset passwords every few months because it was better for security?
Yes, but that was way back in 2014. Starting late 2015, there was a big push from government departments across the world – ranging from UK spy agency GCHQ to US standard-setting National Institute of Standards and Technology (NIST) and consumer agency the Federal Trade Commission (FTC) – to not do that.
That said, the past few years has been virtually defined by the loss of billions of usernames and passwords from corporations, ranging from your email provider, to your credit agency, home improvement store, retail store and, yes, even government departments.
In that case, does it not in fact make sense to get people to periodically change their passwords? Well, yes. And no.
Yes, because the information would age and so become irrelevant faster. No, because constant resets eat up resources, tend to nudge people toward using simpler passwords, and don’t really make it harder for some miscreant using a brute force attack to guess the password.
[…]
Random or pronounceable?
Everyone agrees that using the word “password” for a password is pretty much the dumbest thing you can do. But so many people still do it that designers have been forced to hardcode a ban on the word into most password systems.
But from there – where do you go? How much better is “password1”? Is it sufficiently better? What about switching letters to other things, like “p@ssw0rd”? Yes, objectively, that is better. But the point is that there are much better ways. And that comes down to basically two choices: random or pronounceable.
The best random password is one that really is random i.e. not a weird spelling that you quickly forget but a combination of letters, numbers and symbols like “4&bqJv8dZrXgp” that you would simply never be able to remember.
But here’s the thing – the reason that particular password is better is largely because in order to use and generate such passwords, you would likely use a password manager. And password managers are great things that we’ll deal with later.
But here’s the thing: if someone is trying to crack your password randomly they are likely to be using automated software that simply fires thousands of possible passwords at a system until it hits the right one.
In that scenario, it is not the gibberish that is important but the length of the password that matters. Computers don’t care if a password is made up of English words – or words of any language. But the longer it is, the more guesses will be needed to get it right.
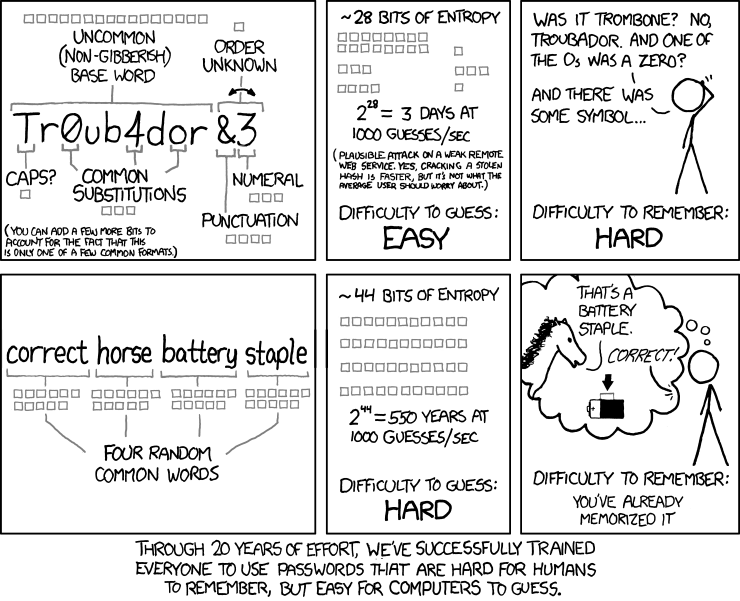
As our dear truthsayer XKCD points out: “Through 20 years of effort we’ve successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
January 18, 2014
How “safe” is your safe?
Safe manufacturers generally ship their products with a factory-standard combination. Many people fail to change them once the safe is in use:
In England many years ago, chatting with a locksmith while he worked, I learned the following thing: One of the country’s leading manufacturers of safes shipped all its products set to a default opening combination of 102030, and a high proportion of customers never reset it.
He: “If I need to open a Chubb safe, it’s the first thing I try. You’d be surprised how often it works.”
This came to mind when I was reading the story about Kennedy-era launch codes for our nuclear missiles:
…The Strategic Air Command greatly resented [Defense Secretary Robert] McNamara’s presence and almost as soon as he left, the code to launch the missile’s [sic], all 50 of them, was set to 00000000.
I use a random-string generator for my passwords and change them often. I guess safeguarding my Netflix account is more important than preventing a nuclear holocaust.
June 11, 2013
The elephant in the IT room – who can you trust?
At The Register, Trevor Pott explains why trust is the key part of your personal online security:
Virtually everything we work with on a day-to-day basis is built by someone else. Avoiding insanity requires trusting those who designed, developed and manufactured the instruments of our daily existence.
All these other industries we rely on have evolved codes of conduct, regulations, and ultimately laws to ensure minimum quality, reliability and trust. In this light, I find the modern technosphere’s complete disdain for obtaining and retaining trust baffling, arrogant and at times enraging.
Let’s use authentication systems as a fairly simple example. Passwords suck, we all know they suck, and yet the majority of us still try to use easy to remember (and thus easy to crack) passwords for virtually everything.
The use of password managers and two-factor authentication is on the rise, but we have once more run into a classic security versus usability issue with both technologies.
[. . .]
Trust as a design principle
The technosphere doesn’t think like this. Very few design their products around trust, or the lack thereof. We’ve become obsessed with how the technology works and what that technology can enable; technology is easy, people are hard. How the technology we create integrates into the larger reality of politics, law, emotion and the other people-centric elements, is often overlooked.
In some cases it is simply a matter of having a limited target audience; American firms designing for American users, for example. It is impossible for most to really understand the intricacies of trust issues in all their variegated permutations. It is human to be limited in our vision, and scope of understanding.
H/T to Bruce Schneier for the link.
October 27, 2012
Do you use a stupidly easy-to-guess password?
SplashData has released an updated list of the top 25 passwords gleaned by hackers from stolen password files:
# Password Change from 2011 1 password Unchanged 2 123456 Unchanged 3 12345678 Unchanged 4 abc123 Up 1 5 qwerty Down 1 6 monkey Unchanged 7 letmein Up 1 8 dragon Up 2 9 111111 Up 3 10 baseball Up 1 11 iloveyou Up 2 12 trustno1 Down 3 13 1234567 Down 6 14 sunshine Up 1 15 master Down 1 16 123123 Up 4 17 welcome New 18 shadow Up 1 19 ashley Down 3 20 football Up 5 21 jesus New 22 michael Up 2 23 ninja New 24 mustang New 25 password1 New
If you recognize any password on this list … do yourself a favour and change it to something not on the list, preferably using more characters (including upper and lower case letters, numbers, and symbols). And don’t use the same password on multiple sites! SplashData sells a password keeper application that is quite useful (I’ve been using it for years now), and is available for multiple platforms.
July 12, 2012
Säkerhetsbloggen does some preliminary analysis of Yahoo’s 453,000 leaked passwords
As we’ve noticed before, there are lots of really, really bad passwords in use:
Recently, Ars Technica reported about a leak by “D33ds Company” of more than 450.000 plain-text accounts from a Yahoo service, which is suspected to be Yahoo Voice.
Since all the accounts are in plain-text, anyone with an account present in the leak which also has the same password on other sites (e-mail, Facebook, Twitter, etc), should assume that someone has accessed their account.
[. . .]
Total entries = 442773 Total unique entries = 342478 Top 10 passwords 123456 = 1666 (0.38%) password = 780 (0.18%) welcome = 436 (0.1%) ninja = 333 (0.08%) abc123 = 250 (0.06%) 123456789 = 222 (0.05%) 12345678 = 208 (0.05%) sunshine = 205 (0.05%) princess = 202 (0.05%) qwerty = 172 (0.04%)
Other bits of password-related idiocy are here.
November 19, 2011
Internet users’ password security still hasn’t improved
Do you use any of the following terms as your password? If so, congratulations, you’re helping keep the rest of us from being as easily hacked as you are:
1. password
2. 123456
3. 12345678
4. qwerty
5. abc123
6. monkey
7. 1234567
8. letmein
9. trustno1
10. dragon
11. baseball
12. 111111
13. iloveyou
14. master
15. sunshine
16. ashley
17. bailey
18. passw0rd
19. shadow
20. 123123
21. 654321
22. superman
23. qazwsx
24. michael
25. football
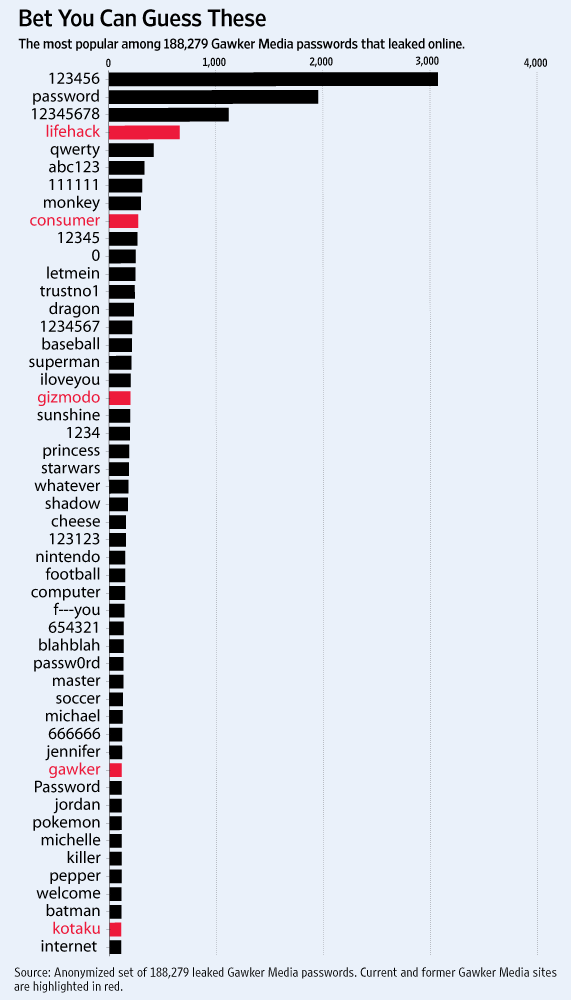
This list is from SplashData, who produce (among other things) a password-keeper utility. Last year, Gawker published the 50 top passwords in a graphic:
Here’s a word cloud from an earlier post on passwords:

Other posts on this topic: opportunities for humour with your bank’s secret questions, xkcd on the paradox of passwords, Passwords and the average user, More on passwords, And yet more on passwords, and Practically speaking, the end is in sight for passwords.
September 9, 2011
Opportunities for humour with your bank’s “secret questions”
If you do online banking, you’ve probably been asked to provide additional security checks beyond your userid and password. Some banks only allow you to select answers from pre-selected questions, but others get you to provide both the question and the answer. In a post from more than a year back, Bruce Schneier offers a few combinations that lighten the mood (and there are lots of funny — and weird — suggestions in the comment thread):
Q: Need any weed? Grass? Kind bud? Shrooms?
A: No thanks hippie, I’d just like to do some banking.Q: What the hell is your fucking problem, sir?
A: This is completely inappropriate and I’d like to speak to your supervisor.Q: I’ve been embezzling hundreds of thousands of dollars from my employer, and I don’t care who knows it.
A: It’s a good thing they’re recording this call, because I’m going to have to report you.Q: Are you really who you say you are?
A: No, I am a Russian identity thief.
August 10, 2011
xkcd on the paradox of passwords
July 11, 2011
Can the government force you to provide your password?
Declan McCullagh discusses a potentially precedent-setting case in Colorado that may determine whether the 5th amendment applies to your personal passwords:
The Colorado prosecution of a woman accused of a mortgage scam will test whether the government can punish you for refusing to disclose your encryption passphrase.
The Obama administration has asked a federal judge to order the defendant, Ramona Fricosu, to decrypt an encrypted laptop that police found in her bedroom during a raid of her home.
Because Fricosu has opposed the proposal, this could turn into a precedent-setting case. No U.S. appeals court appears to have ruled on whether such an order would be legal or not under the U.S. Constitution’s Fifth Amendment, which broadly protects Americans’ right to remain silent.
I’d hope that the protections against self-incrimination would apply in this case, but government power has been expended so far in the last ten years that it would not surprise me if the courts gut this right in their deference to the executive (just like every other time, it seems).
May 2, 2011
I think I’ll hold off on buying a PlayStation for a little while longer
I actually was considering buying a PS3 in the near future, as our existing Blu-Ray player doesn’t play nicely with Netflix, while my domestic gaming advisor tells me that PS3’s do. Sony’s security problems are enough to give me pause:
“It’s really scary,” said Marsh Ray, a researcher and software developer at two-factor authentication service PhoneFactor, who fleshed out the doomsday scenario more thoroughly on Monday. “It’s justification for Sony freaking out. They could lose control of their whole PS3 network.”
Ray’s speculation is fueled in part by chat transcripts that appear to show unknown hackers discussing serious weaknesses in the PSN authentication system. In it, purported hackers going by the handles trixter and SKFU discuss how to connect to PSN servers using consoles with older firmware that contain bugs susceptible to jailbreaking exploits, even though Sony takes great pains to prevent that from happening.
“I just finished decrypting 100% of all PSN functions,” SKFU claimed.
There’s no evidence the participants had anything to do with the massive security breach that plundered names, addresses, email addresses, passwords and other sensitive information from some 77 million PSN users. But the log did raise questions about the security of the network, since it claimed it was possible to fool the PSN’s authentication system into permitting rogue consoles.
On this reading, arrogance on the part of Sony executives, and complacency on the part of developers and testers are key elements of the security failure:
“If you can’t jailbreak it, then I can see a developer assuming that they don’t need a particular authorization check on what’s coming across the wire because a user can’t do that,” said WhiteHat Security CTO Jeremiah Grossman, an expert in web application security. “So if somebody managed to jailbreak their device and pop a flaw, I can see something major happening there.”
Hotz, the PS3 jailbreaker who recently settled the copyright lawsuit Sony brought against him, said in a recent blog post that the theory is plausible and that responsibility for the hack lay squarely on the shoulders of Sony executives who placed too much trust in the invulnerability of the PS3.
“Since everyone knows the PS3 is unhackable, why waste money adding pointless security between the client and the server?” Hotz, aka GeoHot, wrote. “This arrogance undermines a basic security principle, never trust the client. Sony needs to accept that they no longer own and control the PS3 when they sell it to you.”
December 14, 2010
No surprises at all in Gawker’s 50 most-popular passwords
An article in the Wall Street Journal has the 50 most popular passwords from the Gawker data heist:

Recognize the pattern? Here’s a word cloud from my last post on passwords:

Other posts on this topic: Passwords and the average user, More on passwords, And yet more on passwords, and Practically speaking, the end is in sight for passwords.
September 15, 2010
Recognize your password?

Password Authentication Tag Cloud
Earlier posts on this topic: Passwords and the average user, More on passwords, And yet more on passwords, and Practically speaking, the end is in sight for passwords.
H/T to Bruce Schneier for the link.
August 16, 2010
Practically speaking, the end is in sight for passwords
Advances in computing are not always uniformly beneficial: short passwords are increasingly vulnerable to brute-force cracking:
The availability of password-cracking tools based on increasingly powerful graphics processors means that even carefully chosen short passwords are liable to crack under a brute-force attack.
A password of less than seven characters will soon be “hopelessly inadequate” even if it contains symbols as well as alphanumerical characters, according to computer scientists at the Georgia Tech Research Institute. The security researchers recommend passwords at least 12 characters long.
The number crunching abilities of graphics processors were recently applied to commercial password auditing and recovery tools from Russian developer ElcomSoft. It’s a safe assumption that black hats are able to use the same type of technology for less laudable purposes. Richard Boyd, of the Georgia Tech Research Institute, told the BBC that the number-crunching capacity of graphics cards compares to those of supercomputers built only 10 years ago.
Passwords are going to go away, sooner rather than later. All of us have too many passwords to remember that it’s pretty much guaranteed that you’re using one of the following coping strategies:
- Using the same password on many different sites (or, shudder, all of them)
- Using a simple password (among the most commonly used are “password” and “letmein”)
- Leaving a sticky note on your monitor or your keyboard with your passwords listed
- Using the name of the site as your password for that site
There are tools available to generate passwords that avoid the most obvious pitfalls (too short, no numeric or non-alphanumeric characters, using full words), but very few people use them consistently. I don’t know what the replacement for passwords will be, but we clearly need to move to more secure ways of verifying identity as soon as we can.
May 4, 2010
Spear phishing (test) attack on US Air Force
I’d heard the term “phishing” before, and I’ve reported at least a dozen various attempts to the appropriate parties (companies and organizations who are used in phishing attempts often have a reporting address set up so you can just forward the message to them). “Spear phishing” was new to me, and apparently it was also new to a large number of US Air Force personnel:
Offers to hire American airmen, stationed at an airbase on the Central Pacific island of Guam, as extras in the Transformers 3 movie, turned out to be an unexpectedly scary training exercise. First, keep in mind that there is no Transformers 3 filming scheduled for Guam. The email was a fake, used to test how well airmen could detect a hacker attempts to deceive military Internet users to give up valuable information.
The Transformers 3 email was a test to see how many airmen would fall for a “spear phishing” offensive. “Phishing” (pronounced “fishing”) is when a hacker sends out thousands, or millions, of emails that look like warnings from banks, eBay or PayPal, asking for you to log in (thus revealing your password to the hackers, who have set up a false website for this purpose) to take care of some administrative matter. The hacker then uses your password to loot your account. “Spear phishing” is when the emails are prepared with specific individuals in mind. The purpose here is to get specific information from, say, a bank manager, or someone known to be working on a secret project. In the Guam case, the targets of the spear phishing test were asked to go to a web site and fill out an application form to be eligible to be an extra. That form asked for information that would have enabled hostile hackers to gain more access to air force networks. A lot of the airmen who received the Transformers 3 email, responded. The air force won’t say how many, but it was more than expected. A lot more.
I doubt that many readers need to be told this, but no legitimate bank or financial institution should ever be sending you an email requesting you to follow an embedded link and log in to your account. If you get such an email, forward it to the bank’s security folks. If it’s legitimate, they can confirm it for you, but in 2010, no sensible bank should be communicating with you in this way.